Illumio has been steadily improving their product since I first encountered the company several years ago, extending its microsegmentation approach as customer demand required.
The core idea of Illumio—microsegmentation using native host-based mechanisms with a centralised control plane—remains a good and useful way of doing things. Tweaks to the GUI have kept it familiar, but markedly better, such as colour vision deficiency adjustments, clearer iconography, and subtle layout changes that make labels easier to find and read.
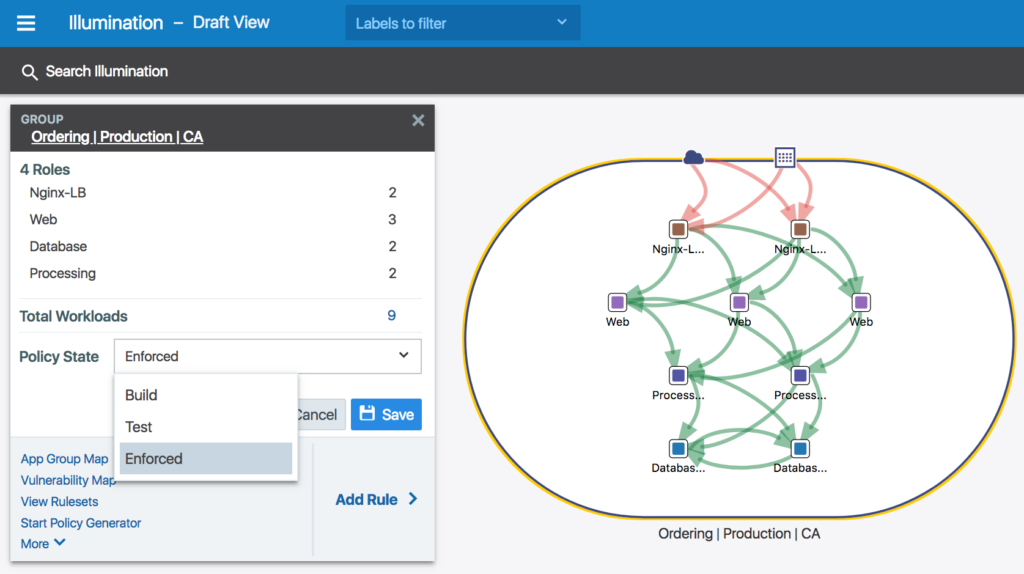
An example of the enhanced Illumio GUI.
Making The Secure Way The Easy Way
Illumio works by making it easier to use what you already have. For Linux hosts, you already have iptables to allow or block traffic, so Illumio configures iptables on the hosts for you. On Windows, there’s an inbuilt firewall as well, so Illumio uses that native Windows firewall to block or allow traffic. Illumio now also supports AIX and Solaris, where ipfilter is the native tool. Illumio also supports certain network equipment, like F5 load-balancers, again using the native capabilities to block or allow traffic between endpoints.
What Illumio really adds is a way to understand how to manage the hundreds or thousands of individual firewalls that are out there but that mostly go unused. Maintaining lots of firewalls is hard work, and humans tend to avoid doing hard things. By making the secure way to do things the easy way to do thing, Illumio helps the humans running the system to adopt more secure practices.
Connections between systems need to happen, and trying to manually maintain firewall rules just results in too many accidents where important traffic gets dropped, or it takes too long to figure out the correct syntax to make the new developer environment accessible to the development team who are sitting around complaining about the security team taking forever. Far too often the solution is to make the immediate problem go away with an allow any any rule that makes everything less secure, but people can continue getting their work done.
Microsegmentation of Microworkloads
The standard host-based firewall approach works fine if you have a regular process=port mapping where allowing access to a given TCP port, but now that we’re seeing container-based deployment and auto-scaling operations of highly dynamic environments, the policy operations of Illumio needed a bit of a refresh.
Policies based on a static list of IP addresses, for example, doesn’t really work when you can add and remove nodes in a Kubernetes cluster that need to be added to the policy. You can also have new applications spin up with copied credentials that start accessing the wrong database causing mayhem and destruction.
Illumio has adapted to the world of containers by providing a containerised version of the Virtual Enforcement Node agent software that makes Illumio work on hosts. The C-VEN works as a DaemonSet so it autoscales with the cluster, but provides a per-container enforcement point that aligns connectivity with the endpoints that need it.
The rest of Illumio’s interface and policy configuration engine continues to work in the same way as for everything else, so Kubernetes clusters become just another resource that Illumio can manage, which makes it easier for security teams to support Kubernetes with the same processes and procedures they already use for other systems.
Where To Next?
I’d like to see Illumio adopt eBPF on Linux to improve performance and take advantage of some of the magic that eBPF offers on the platforms that support it. eBPF is too hard to use directly, but driving it from Illumio would make it easy for me to migrate from iptables which is looking a bit dusty now.
I’d also like to see support for more modern VPN approaches like Wireguard and Host Identity Protocol. This could help us move on from the very IPv4-centric view of connection security that dominates thinking at the moment, particularly in network security circles. Change is hard, particularly when new ways of doing things are more complex to set up. Learning takes time, and time-poor network admins will tend to retreat to the way they already know and trust will work if their early attempts result in too many failures.
Enterprise needs stuff that interoperates with what’s already there, which Illumio does well, but they also need an easy migration path to new approaches. There’s a tremendous opportunity here for Illumio to provide that pathway.
Disclosure: Illumio is a past client of PivotNine and they sent me some Illumio-branded pens, a notebook, and travel mug as part of a TFD22 swag pack. I assume the travel mug is for the lengthy commute between my kitchen and my home office that is about as far as I go these days.




Pingback: Illumio Adds Microsegmentation of Microworkloads - Tech Field Day